
Top Key Microsoft Defender Security Improvements at Ignite 2025 (Part 2)
This is part 2 of showing what Microsoft Ignite 2025 spotlighted, with major cloud security advancements for Microsoft Defender, focusing on unified management, serverless protection, and expert-led services, these updates empower organizations to secure cloud-native applications, enforce compliance, and respond rapidly to evolving threats all from a single integrated platform.
- /
- Knowledge hub/
- Top Key Microsoft Defender Security Improvements at Ignite 2025 (Part 2)
- Knowledge hub
- /Top Key Microsoft Defender Security Improvements at Ignite 2025 (Part 2)

Integration of Defender for Cloud with GitHub Advanced Security
Microsoft Ignite 2025 introduced a game-changing integration between Microsoft Defender for Cloud and GitHub Advanced Security (GHAS), now available in preview. This integration connects your source code repositories directly to cloud workloads, providing unified security visibility across your entire development lifecycle from code commit to production deployment.
Smart Code-to-Cloud Mapping
When you connect your GitHub organization or repository to Microsoft Defender for Cloud, the system automatically maps source repositories to running cloud workloads using proprietary "Code 2 Cloud" methods. This ensures that every deployed application is tracked back to its origin repository and vice versa, providing instant end-to-end visibility. You can see exactly which code powers each production workload, eliminating the need for manual mapping and reducing the risk of blind spots in your security posture.
Production-Aware Alert Prioritization
This integration cuts through the noise of traditional security alerts by prioritizing vulnerabilities based on real runtime context. GHAS findings in GitHub are dynamically linked to runtime risks identified in Defender for Cloud, such as Internet Exposure, Sensitive Data processing, Critical Resources, and Lateral Movement. Security teams can filter, triage, and act only on issues that have actual production impact, helping your team stay efficient and keep your most critical applications secure.
Unified AI-Driven Remediation
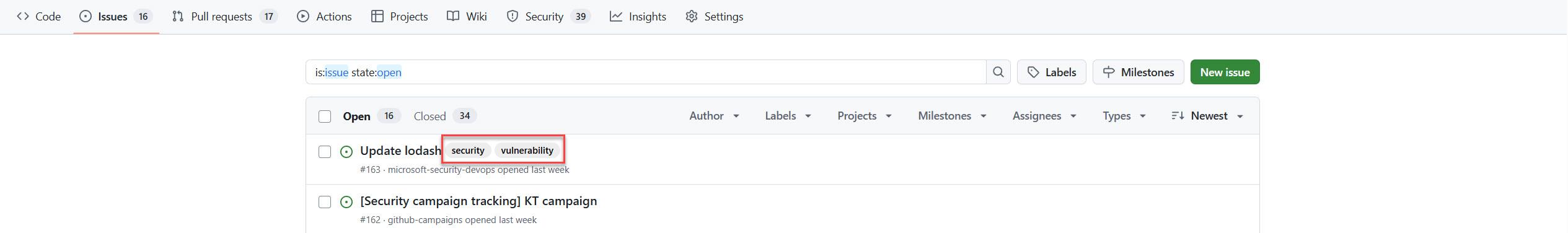
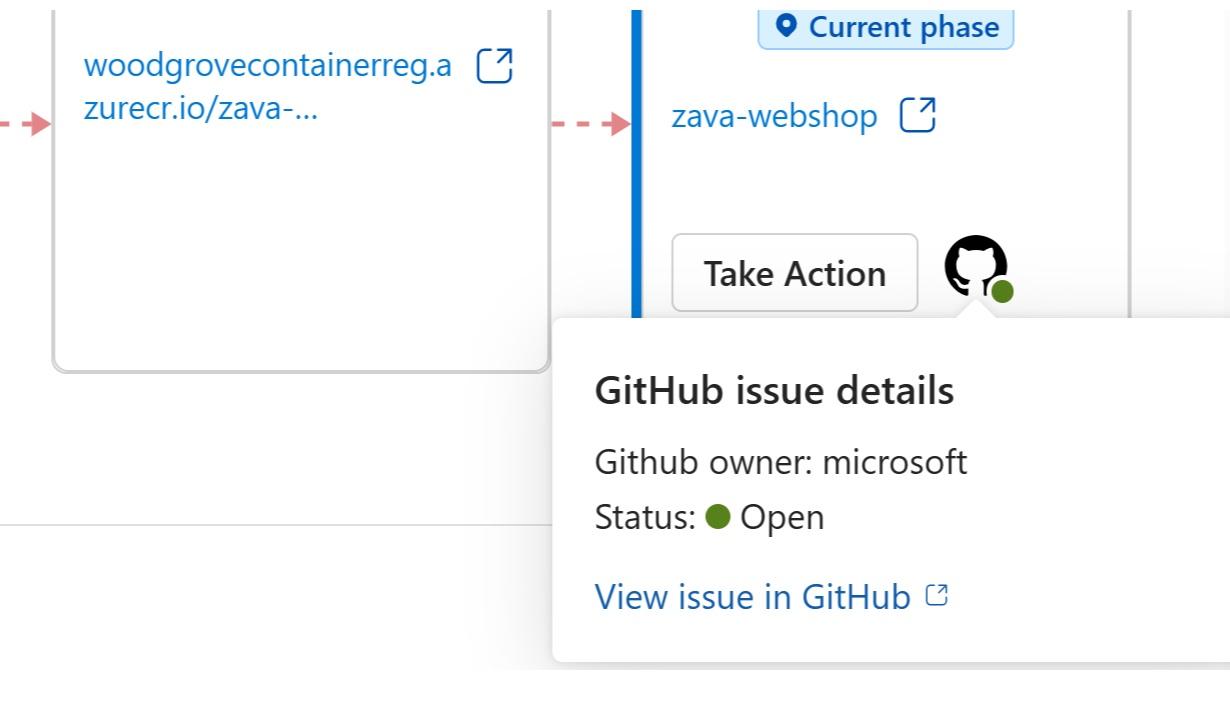
The integration bridges the gap between security and engineering teams with streamlined workflows and relevant context. In Defender for Cloud, security managers can see which issues engineering teams are already aware of and their resolution status by selecting the "View on GitHub" link.
![]()
Security recommendations can be assigned to engineering teams via GitHub issue assignments, generated on the repository of origin with full runtime context to facilitate faster fixes.
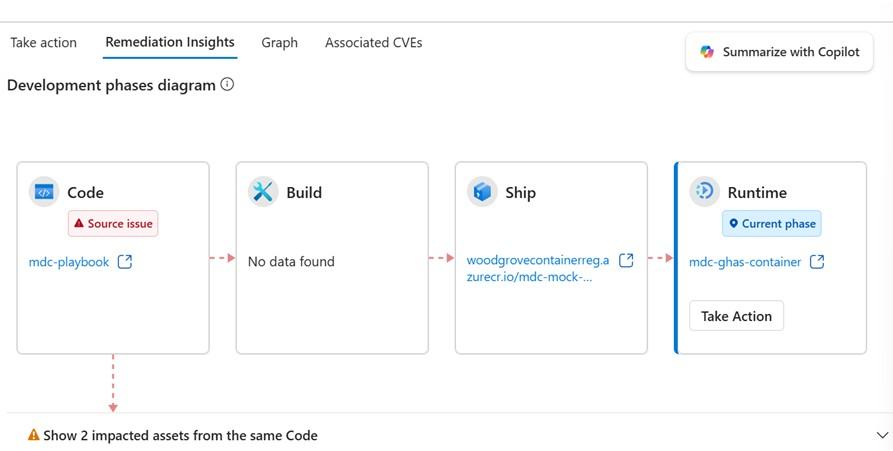
Engineering managers can assign issues to developers, who can then leverage GitHub Copilot Coding Agent for AI-powered autofixes.
Issue fixes, progress, and campaign advancements are tracked in real time, with statuses reflected in both GitHub and Defender for Cloud.
This approach ensures rapid remediation, clear accountability, and seamless collaboration, all within the tools your teams already use.
Implications for Security and Compliance
By unifying code scanning with cloud runtime threat detection, organizations can prevent vulnerable code from reaching production and quickly mitigate live threats. Critical alert prioritization ensures that compliance and security teams address the most dangerous issues first, reducing noise from false positives.
For compliance, having an end-to-end audit trail from code to cloud helps demonstrate controls over the software development process, which is essential for frameworks like SOC 2 and ISO 27001. This integration fosters a DevSecOps culture, where security is embedded into the entire app lifecycle, improving both security posture and compliance with secure development practices.
Posture Management for Serverless Resources in Defender for Cloud
Microsoft Defender for Cloud is addressing a critical gap in cloud security by extending its Cloud Security Posture Management (CSPM) capabilities to serverless resources. With serverless services becoming increasingly popular, traditional security tools often struggle to monitor these dynamic environments. This new feature, available in preview from late November 2025, gives security teams better visibility and control over serverless computing environments that were previously hard to monitor.
Comprehensive Visibility Across Multicloud Serverless Workloads
This update delivers comprehensive visibility into serverless workloads across multicloud environments, including Azure Functions, Azure App Service (Web Apps), and AWS Lambda. As organizations shift from traditional VMs to serverless architectures, this capability ensures that security posture management evolves alongside their infrastructure. The system identifies misconfigurations, insecure settings, or vulnerabilities in these ephemeral resources, common entry points for attackers so security teams can act before threats escalate.
Serverless Specific Insights and Attack Path Analysis
Defender for Cloud now includes serverless specific insights, providing security teams with a complete inventory of serverless functions and apps. These are integrated into attack path analyses, allowing defenders to see how weaknesses in serverless resources could be exploited.
For example, if a function has an overly permissive role or an unpatched vulnerability, Defender highlights the potential for exploitation in an attack chain. The tool continuously monitors for risky deployments, such as functions with public endpoints that should not be, and flags these on a central dashboard. Admins can visualize risks and even simulate how an attacker might move laterally via serverless components, which often communicate with databases, storage, and other critical services.
Security and Compliance Implications
Bringing serverless into cloud posture management enables organizations to enforce consistent security policies across all workloads, including serverless functions. This reduces the risk of unnoticed misconfigurations exposing sensitive data.
For compliance, regulations like PCI DSS and HIPAA require securing all cloud resources. This feature demonstrates that even serverless components are actively monitored and governed. By closing security gaps, organizations strengthen their cloud security baseline and bolster end to end compliance as they adopt more serverless and PaaS services. Overall, this capability reduces risk in modern application architectures and helps ensure that security keeps pace with innovation.
Unified Cloud Security Posture in a Single Defender Portal
Microsoft has announced that its Defender for Cloud capabilities will be integrated into the Microsoft Defender (XDR) portal to provide a single, unified experience for security teams. This preview update means security analysts no longer need to switch between the Azure Portal and Defender portals; instead, they will access a centralized dashboard for comprehensive cloud security posture and threat protection.
Comprehensive Visibility Across Multicloud Environments
The new Cloud Security Dashboard consolidates cloud posture management and threat detection across multiple cloud providers, including Azure, AWS, and Google Cloud. Security teams can view all cloud assets, configurations, vulnerabilities, attack paths, and active threats in one place. Built-in Exposure Management features display a organization’s secure score, inventory of vulnerable assets, misconfigurations, prioritized recommendations, and potential attack chains, enabling rapid identification of high-risk resources and prompt response without switching tools.
Centralized Inventory and Role-Based Access Control
The experience provides a central asset inventory covering resources across different cloud environments, including VMs, containers, and serverless functions. This comprehensive inventory supports easier compliance audits, as teams can export lists of assets and their security statuses. Additionally, granular role-based access control (RBAC) ensures only authorized personnel can view or manage specific resources, maintaining proper duty segregation in multi-tenant or multi-team scenarios.
Security and Compliance Implications
This unification removes the fragmented views and tool silos that previously hampered detection and response efficiency. Analysts can now see threats across all cloud workloads in one interface, enabling consistent response actions.
For compliance, having posture management and threat alerts integrated into a single portal facilitates faster, more comprehensive reporting. Security leaders can easily generate reports on overall cloud security health, compliance status, and configuration benchmarks, simplifying adherence to frameworks like CIS and other cloud-specific regulations. This integrated approach ultimately enhances SOC efficiency and ensures no cloud resource escapes security oversight.
Microsoft Defender Experts Suite (Expert Led Services)
Microsoft has announced the Defender Experts Suite, set for early 2026 availability. This new offering combines human led managed services with Microsoft’s advanced security technology, making it a significant update to the Defender family. The suite packages managed extended detection and response (MXDR), proactive threat hunting and incident response services, and dedicated expert support into a single subscription.
Purpose and Value for Organizations
The main goal is to help organizations that lack large security teams by allowing them to outsource some of their defense to Microsoft experts, enhanced by AI. Microsoft’s security advisors and responders work alongside the customer’s Defender tools to defend against threats and respond rapidly to incidents. Notably, Microsoft has also announced partnerships, such as serving as an approved incident response partner for cyber insurance providers, to streamline incident handling.
Security and Compliance Implications
For organizations pursuing compliance or cybersecurity certifications, leveraging the Defender Experts Suite can help fulfill requirements for continuous monitoring and incident response readiness.
By using certified experts, organizations gain credibility and may reduce the impact of major incidents, supporting compliance with breach of notification and containment obligations. This service underscores that Microsoft Defender provides not only automated tools but also expert services for a holistic defense. It increases confidence in adopting advanced features, knowing that experts can assist in their use and in handling complex threats.
Conclusion
Microsoft Defender from Ignite 2025 focuses on AI-driven, integrated security, linking development with runtime protection, monitoring all cloud and hybrid assets in one platform, and enhancing the SOC with predictive defenses and Copilot agents.
These updates improve breach of prevention and compliance, enabling organizations to better secure data across code, cloud, and AI systems with greater visibility and faster responses.
To maximize these benefits, contact our expert at Precio Fishbone for tailored solutions.
Additional updates are covered in Part 1
