
Microsoft Defender at Ignite 2025: Top New Security Improvements (Part 1)
Microsoft Ignite 2025 brought major announcements for security teams. This year's focus: empowering customers with advanced features within their existing Microsoft tools, which can significantly strengthen your security operations.
This report outlines the new features and updates unveiled at Ignite 2025 for Microsoft Defender. Each section below offers structured overviews of these features, explaining what they are, their purpose and capabilities, and their impact on organizational security and compliance.
- /
- Knowledge hub/
- Microsoft Defender at Ignite 2025: Top New Security Improvements (Part 1)
- Knowledge hub
- /Microsoft Defender at Ignite 2025: Top New Security Improvements (Part 1)

What is Microsoft Defender?
Microsoft 365 Defender serves as a unified platform that enables comprehensive monitoring and management of security throughout your entire enterprise. It delivers integrated alerts spanning critical domains including identities, endpoints, data, applications, email, and collaboration tools for a holistic view of potential risks.
This solution empowers you to investigate and respond to threats efficiently from a single centralized location, while proactively preventing, detecting, remediating, and investigating incidents across Microsoft 365 to safeguard modern hybrid organizations and thwart cybercriminals attempting user impersonation.
Innovations in Ignite 2025
Microsoft Defender, the core of Microsoft’s threat protection suite, gained major upgrades at Ignite 2025, designed to enable more autonomous, AI powered security defenses. These enhancements cover seamless integration into development pipelines, broader cloud protection, AI agent safeguards, unified cloud posture management, and cutting-edge threat disruption tools. Collectively, they bolster proactive defenses while easing the burden on security teams.
AI Agent Security in Microsoft Defender
The Rising Threat: Why AI Agents Need Protection Now
AI agents are exploding across enterprises creating massive blind spots as shadow agents process sensitive data without oversight exposing firms to prompt injection attacks, data leaks and compliance risks. These autonomous bots, whether custom coded low code Power Platform creations or simple no code tools built by business users often handle personal information, make autonomous decisions or access critical systems yet fly under traditional security radar.
Ignite 2025 addresses this crisis head on as Microsoft Defender now treats AI agents as first class security assets through a preview feature in the Microsoft Agent framework delivering unified posture management and threat protection from one central dashboard.
What Unified Posture Management Means for AI Agents
This single pane of glass revolutionizes visibility, giving security teams complete oversight into AI agents running organization wide from sophisticated pro code bots to casual low code and no code experiments. The AI agent posture dashboard automatically inventories all known agents, assesses their security health, checks access controls and permissions, and exposes shadow AI agents operating without governance while providing continuous monitoring.
Security teams see exactly which agents have excessive privileges, which connect to risky external services, all consolidated in Defender, eliminating the chaos of hunting across multiple tools and preventing hidden risks from silently escalating into major breaches.
Proactive Risk Reduction Through Attack Path Analysis
Defender goes beyond visibility to proactively eliminate risks with AI specific recommendations and attack path analysis tailored to agent vulnerabilities. It simulates realistic exploits like prompt injection where attackers craft malicious inputs to trick agents into spilling database secrets, executing unauthorized API calls or escalating privileges, then delivers precise actionable controls to seal those gaps before real attackers strike.
For instance, if an agent lacks least privilege access to a customer database, Defender maps the full attack chain to high value assets like financial systems, prioritizes remediation steps, and shifts security left by embedding protections directly into the AI development lifecycle. This forward-looking methodology transforms reactive firefighting into systematic prevention, ensuring agent weaknesses never reach production.
Threat Protection: Detecting Real Time Agent Compromises
Active threat protection captures malicious activities targeting agents or originating from compromised ones with surgical precision and speed. A hacker attempting prompt injection on a corporate chatbot to exfiltrate customer data triggers instant anomalous behavior alerts correlated across endpoint signals, network traffic, threat intelligence, and agent specific telemetry.
Alerts surface with rich context, enabling analysts to immediately pivot into investigation and remediation using familiar Defender workflows identical to compromised user accounts or endpoints. These slashes mean time to respond from hours to minutes while blocking lateral movement through agent networks.
Compliance and Governance at Enterprise Scale
The implications for security operations, compliance, and business enablement are profound. AI agents processing sensitive data or driving autonomous decisions now receive the same rigorous human equivalent oversight as traditional users or endpoints, automatically curbing agent sprawl by discovering, onboarding, or quarantining rogue bots before they violate policies.
Shadow AI, the uncontrolled proliferation of unauthorized agents, becomes a solved problem as Defender surfaces these risks early, enabling governance without stifling innovation. Security teams reduce alert fatigue by focusing only on exploitable agent vulnerabilities rather than theoretical risks, while developers build faster knowing security is baked in from design.
Business leaders can scale AI adoption confidently across departments without gambling on unmonitored agents leaking data, triggering fines, or enabling ransomware pivots through compromised bots. This unified approach bridges the gap between rapid AI experimentation and enterprise grade security, creating a mature governance model where innovation accelerates under protection.
The Bottom Line
Microsoft Defender’s AI agent security represents a fundamental shift from treating agents as experimental toys to recognizing them as critical infrastructure demanding user grade protection. By unifying posture management, proactive risk reduction, and real time threat protection in one platform, organizations gain the controls needed to harness AI’s power responsibly at scale while satisfying even the strictest compliance mandates.
Predictive Shielding – Proactive Mid-Attack Defense
Microsoft has introduced a groundbreaking new feature called Predictive Shielding as part of its Microsoft Defender suite. Predictive Shielding is an automatic attack disruption capability that activates immediately after an initial attack is contained.
This innovative feature is the first of its kind to combine graph-based insights, artificial intelligence, and real-time threat intelligence to predict the most likely attack paths an adversary might take next within your environment. By analyzing the relationships between assets, user behaviors, and historical threat patterns, Predictive Shielding can forecast where attackers are likely to pivot after gaining initial access.
Works in two clear steps
Step 1: Predicting Attack Paths
As soon as a compromised asset is contained, Defender uses advanced AI to predict the most likely attack paths and tactics the attacker will try next. This process narrows down thousands of possible routes to only the most probable ones.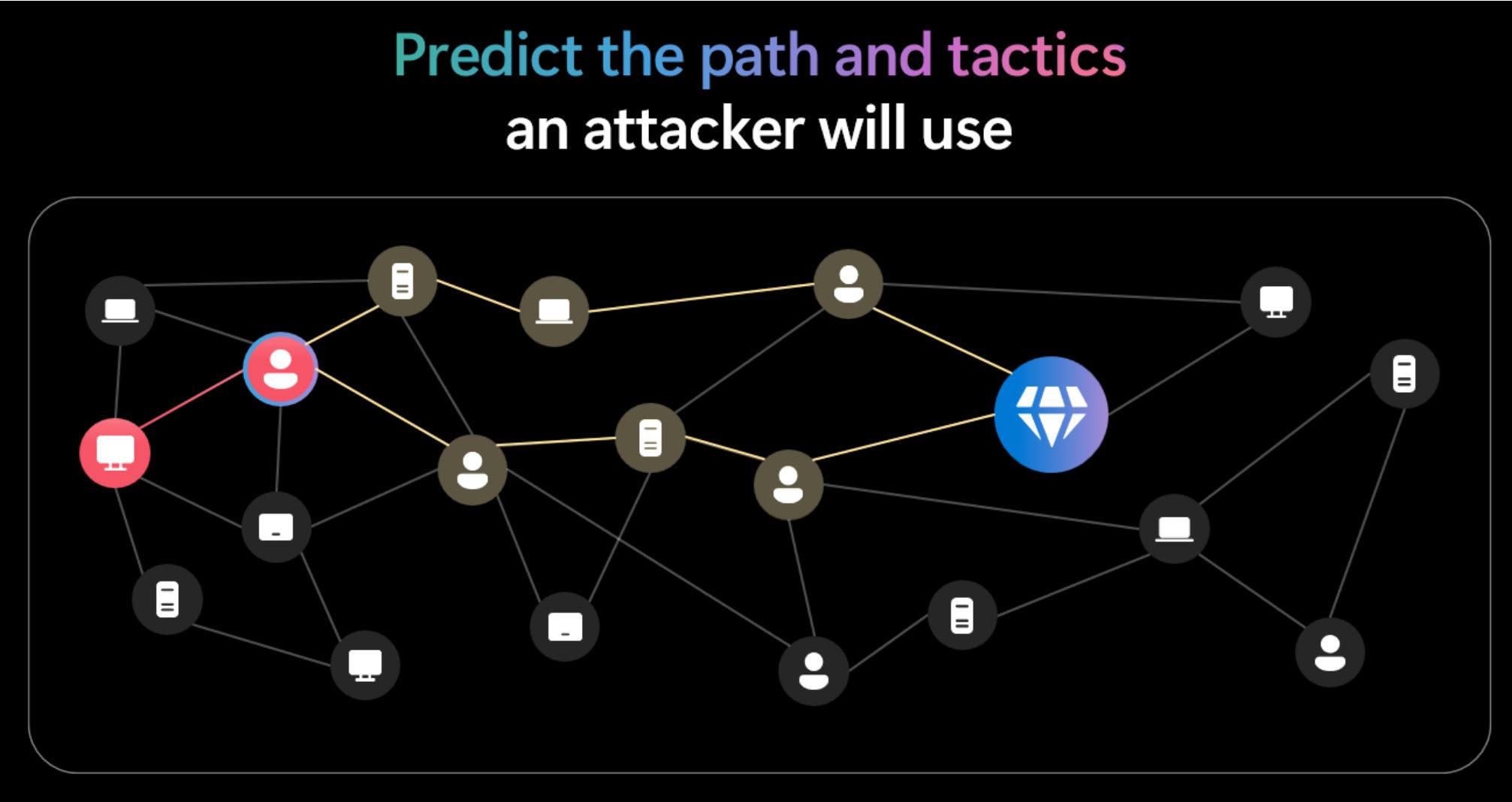
Step 2: Shielding Predicted Pathways
Defender then proactively blocks these predicted pathways by applying targeted hardening measures in real time, leaving the attacker with no viable options to move forward.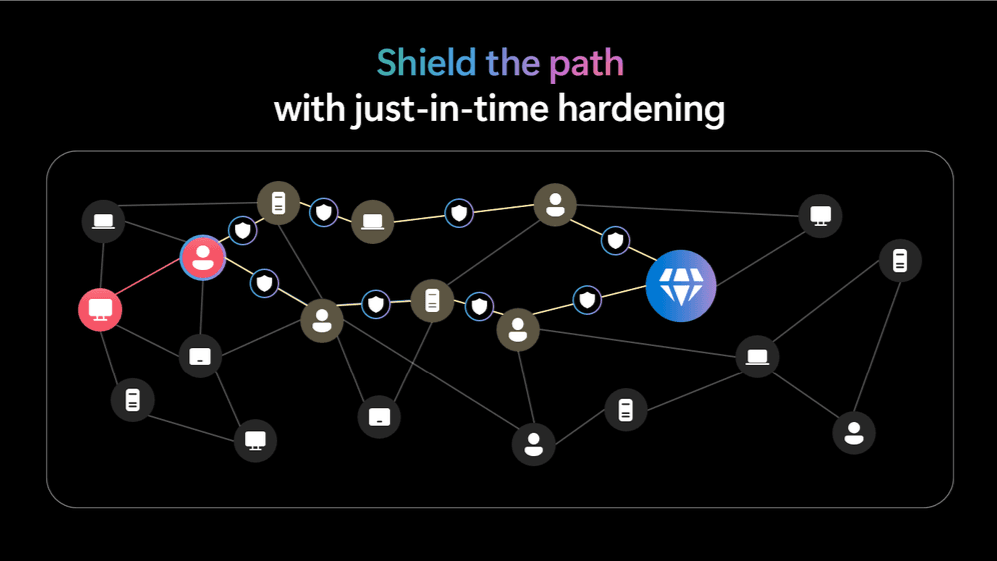
Once potential attack paths are identified, Defender applies just-in-time hardening to block lateral movement. It locks down likely targets before attackers can reach them, using actions like enforcing Group Policy Objects, and tightening firewall rules. These measures focus on the most probable threats, minimizing disruption while maximizing protection.
By integrating AI and graph analytics, Predictive Shielding gives security teams a time advantage against fast-moving threats. It stops techniques like credential theft, privilege escalation, and data exfiltration before they happen, reducing the attacker’s window and strengthening resilience and compliance.
AI-Powered Threat Hunting Agent in Defender
Microsoft Defender introduces a new Threat Hunting Agent as part of its Security Copilot integration, designed to empower security analysts with advanced threat hunting capabilities. This agent enables users to perform complex threat investigations using simple, natural language queries, making the process accessible even to those without deep expertise in query languages like KQL.
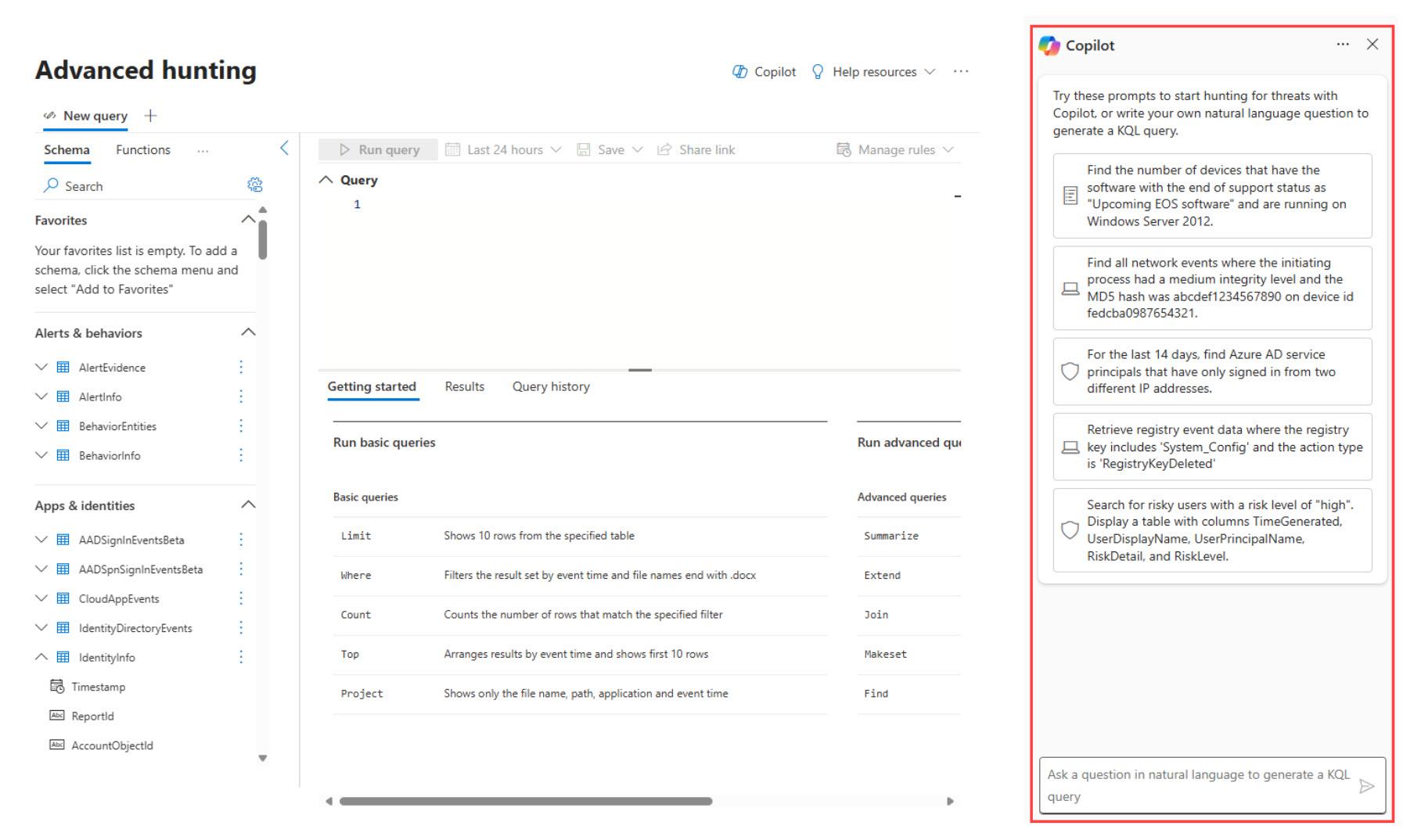
In the Microsoft 365 Defender portal, analysts can open a dedicated Security Copilot chat interface. They can ask questions in plain English such as “Show me any devices that communicated with this suspicious domain in the last 24 hours.” The Threat Hunting Agent interprets the query, automatically crafts and runs the appropriate KQL or other log queries, and returns a summarized answer with supporting data. The agent goes beyond single answers by dynamically suggesting follow-up questions or actions, guiding analysts through a logical investigation flow.
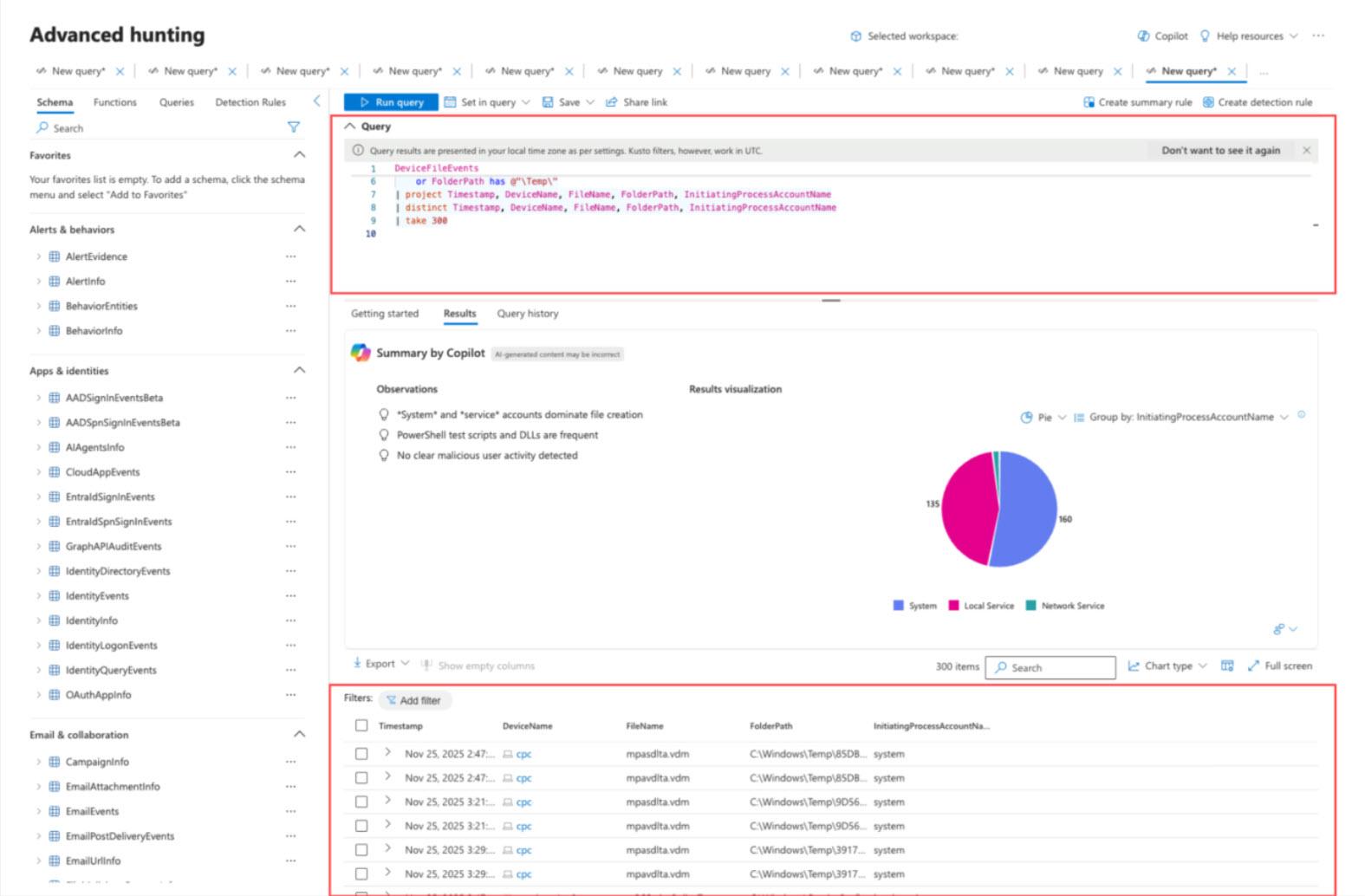
The agent provides contextual insights and visualizations, such as timelines or connection charts, to clarify findings. It also exposes the underlying KQL used, allowing advanced users to tweak or learn from the queries. This means junior analysts can perform sophisticated hunts, while senior analysts can validate and refine the AI’s approach. The agent acts as a copilot, handling data-heavy tasks and allowing humans to focus on intuition and decision-making.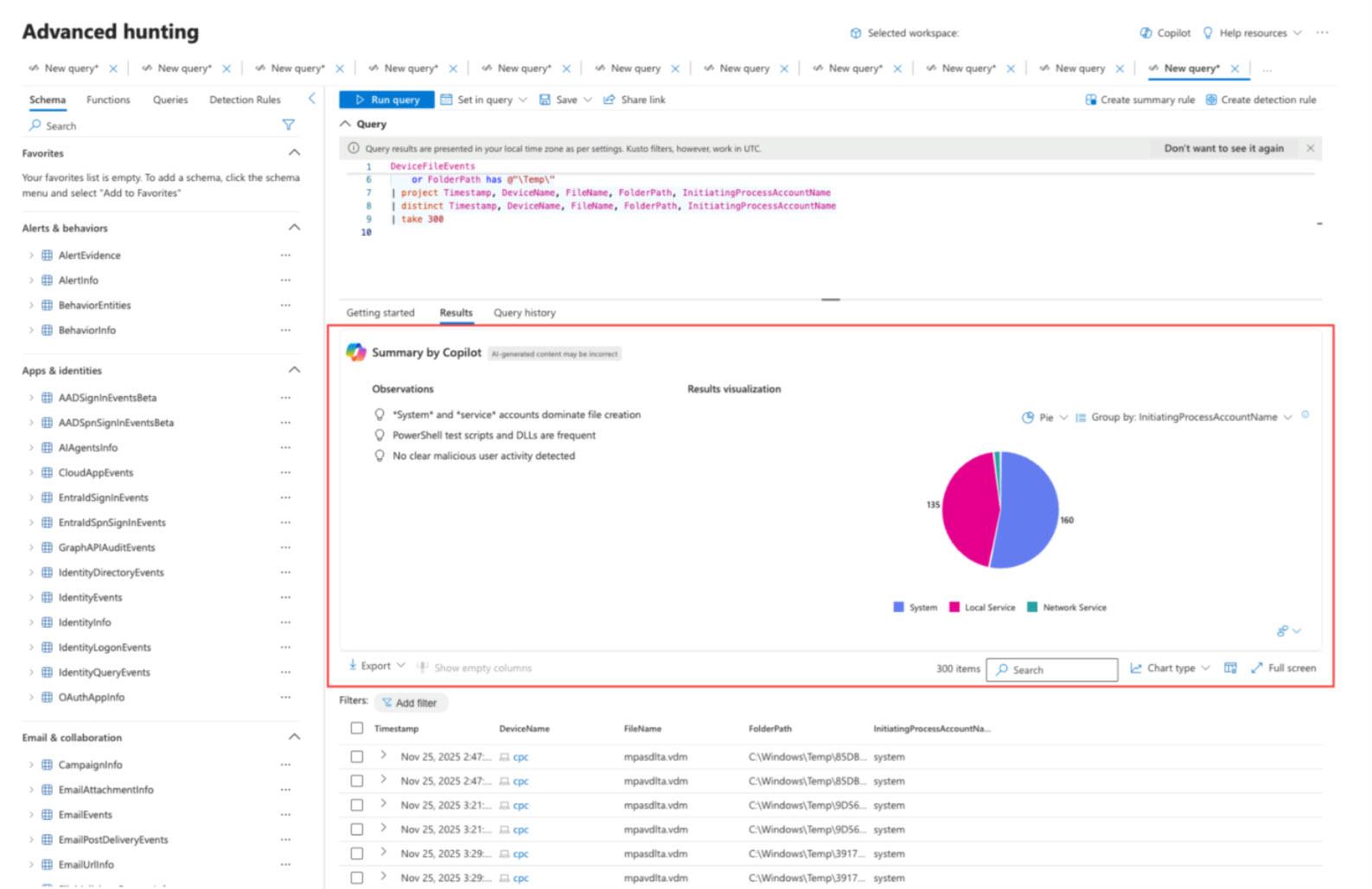
The benefits are significant: faster and broader threat hunting helps uncover “silent” indicators of compromise that automated alerts might miss. After a major incident, teams can quickly use the agent to search for similar techniques elsewhere, closing detection gaps. This proactive approach improves mean time to detect and helps address stealthy attacks before they escalate.
For compliance, the Threat Hunting Agent ensures that potential breaches or malicious activities are overlooked due to skill or resource limitations. Frameworks like NIST or ISO encourage proactive monitoring, and this feature enables it even in resource-constrained teams. The agent’s use of natural language also lowers the barrier to documenting investigations, leaving a clear trail of queries and results as evidence of due diligence. This robust approach contributes to a stronger security posture and supports compliance by reducing the likelihood and impact of undetected incidents.
Optimize your security team workload with Microsoft Defender
With new potential innovations, Defender empowers your team to focus on strategic initiatives rather than routine monitoring and response. By leveraging advanced automation and AI-driven analytics, your organization can detect threats faster, respond more efficiently, and maintain a robust security posture with less operational overhead.
To get the most out of Microsoft Defender and tailor these capabilities to your unique environment, reach out to our expert at Precio Fishbone for customized solutions.
